I'm thankful that I still have both sets of parents, a number of siblings, my wife, my kids, and a number of friends and still-welcome strays (shouts to the Garage Troll) who've passed through our lives in the past year. Here's hoping that you have good fortune and quiet lives in the coming year.
Tuesday, December 25, 2007
Sunday, December 23, 2007
Home down for maintenance
Saturday, December 22, 2007
Augh!!
(heh)
Friday, December 21, 2007
VOIP Users' Conference
For those that aren't familiar with the VUCC, it's a Talkshoe-based conference call held every Friday at noon (EST). I've added the badge for it to the left.
Thursday, December 20, 2007
Port-Sec
The cool thing about this is that we've been holding these dinners for much longer than the whole Bean-Sec/Chi-Sec thing has been going on. This evening's dinner was much more enjoyable because it was a much smaller group. We didn't invite many of the first-year students so the group was able to eat at one large table and we were all able to hear each other (a first!).
The only drawback to the entire evening was the food. Since "Mama" at the Biergarden (in Portsmouth) doesn't "drive" the kitchen any more, the quality of the food has slipped to the point where it's recognizeable that it's German food cooked by someone who's not familiar with it. Authentic German food (that is, good food) has a taste that is based not only on its ingredients, but also how the pans are handled, how the stove is operated, and how the prep surfaces are cleaned. All that I can say is that the Biergarden in Portsmouth, VA is now in dire need of a good German cook. If they don't get one, they risk losing a good-sized chunk of their clientelle. (For anyone that has a German grandmother, here's a hint: I didn't have seconds, not even of the spaetzle.)
For those that didn't attend tonight, you missed a good time (food not withstanding). Hopefully you'll be able to attend in the Spring.
Tuesday, December 18, 2007
Mozilla phone
It appears to be a SIP-based plugin for Firefox and Thunderbird, capable of running on Windows, Mac, and Linux. It also isn't tied to any one service provider like so many other VoIP tools nowadays.
Sooo... It looks like I'll be playing with it in the near future, seeing how well it works with Linux. I'll keep you posted.
Sunday, December 16, 2007
Asterisk and TalkShoe
Wednesday, December 12, 2007
Request for public comments?
A friend's recent vanity search, which turned up some unexpected responses, prompted me to do one of my own (it's been awhile). The short version of this story is that I may not yet have visited Congress, but my words have. Yikes!
Okay, it was a RFC dealing with constraints on how a specific organization should make its data publicly available. Nothing major but what happens to your words, after they leave your head, can be quite interesting.
ACM update
Sunday, December 9, 2007
Saturday, December 8, 2007
System updates
As I'd been planning to experiment with the Jackd Audio Distro (JAD) and Ubuntu Studio, I downloaded and installed them first. In short, there are a number of tools in those distros that I'd like to have running. However, JAD is FC6-based and Unbuntu Studio is a version or two behind. In other words, there are a number of "known" issues that more recent distros have fixed and that I'm not willing to live with.
For me, the remaining choices were FC8 and Mandriva 2008. I've been hearing good things about FC8 and decided to try that first. Sadly, it's still a bit short in detecting hardware, specifically my stock (built-in) NVidia 6xxx video card. It still has the invisible mouse issue and still requires that the NVidia drivers be installed manually, including a number of prerequisites that the beginning user would find near-impossible to install.
So it's back to Mandriva. It detects the video card properly at install and autoloads the kernel modules for it. The Easy Urpmi service is also available which covers for a number of missing packages in the "free" Mandriva distro.
The one shortcoming in Mandriva that I have to work around is a number of odd RPM dependencies, due to the number of RPM authors who maybe didn't do as much due diligence as they should. My work-around: use Easy Urpmi for installing languages and their dependencies. Everything else, build from scratch. For some of the more cutting-edge stuff (e.g., stuff still in development), you have to build from source anyways.
So here I am blogging, while texlive-texmf (a _really_ big bundle) installs via Easy Urpmi and miscellaneous OCaml libraries are compiling from source. This should take most of the morning.....
Friday, December 7, 2007
Music-on-hold Alternatives
In response to an exceedingly bad week of trying to get mpg123 to tolerate some high-end netcasts, I've decided to document alternatives to mpg123.
Thursday, December 6, 2007
With friends like these
Sunday, December 2, 2007
AMI Notes
Tuesday, November 27, 2007
ACM update
The Kick and Mute/Unmute buttons are kinda obvious. The "Muzak" button starts playing music into the conference room. The stream button starts streaming the conference room to a local Icecast server. The "trick" behind these last two buttons is the "Originate" function call in the AMI.
Next up: being able to edit the caller's name and their topic (can you guess where I'm going with this?) and being able to push callers back and forth between queues and conference rooms. Maybe a bridge between conference rooms?
Sunday, November 25, 2007
I R one!
Saturday, November 24, 2007
Further experimentation
It's surprising to see that IPKall and FWD allows more than one concurrent inbound call. I'll need to do a bit more research to figure out what the limits are, both remote and on my system (what with all the other daemons that are running).
Note that I've updated the mute/unmute code.
Thanks for the assist, Sparks!
Disclaimers for "Asterisk Conference Manager"
- The code is GPL'd by the original author. The usual terms apply.
- The original author's disclaimers, and those for the Asterisk Manager Interface (AMI), where the security of this program primarily relies on your ability to limit access to it, still exist.
- The program is written in PHP and AJAX (or what passes for it). I suck at PHP and AJAX. Keep in mind that the program is little more than a page scraper for the AMI. What this means is that the code is likely to be very version-dependant. (I'm running Asterisk 1.4.x.) It works but you can't hold any of the coders responsible for maintaining it. Any changes/updates to the underlying platform will likely break ACM's functions.
- Running this service keeps an open connection on your web server. Firefox and/or IE are likely to be poor choices for browser interfaces for this program. Both are memory hogs and eat up a chunk of memory. I run a lot of crap on the same machine as this one. Heavy use of the underlying web server, with Firefox, does generate audio artifacts. Your mileage will vary.
In any case, please let me know if you find it useful or want to suggest changes.
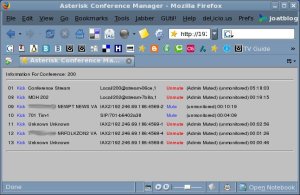
Asterisk Conference Manager
Meetme Manager really didn't fit the bill. I liked the available controls but hated that you had to click on something to update the page. This meant either a local GUI or an Ajax-driven web interface.
Luckily, John at Asterikast had played with an Ajax (I think it's Ajax) interface which maintains a connection to the Asterisk Management Interface (AMI). The drawback to John's script is that it hasn't seen an update since he posted the code last March. I did like the baseline code though, so I've made a few changes.
The major revisions are in the output.php file. There seemed to be a lot of code to perform just a few functions. I've heavily edited that so that it now recognizes local connections and miscellaneous SIP connections that didn't meet the original filter constraints.
John's original code only allowed for kicking users. I've added mute/unmute controls. Currently, it's been demonstrated to handle local internal connections (.call connections for MOH), SIP calls from the local network, and IAX2 calls via IPKall and FWD (Yeah, I call Washington State to connect to my own machine in Virginia Beach. What the heck, it doesn't cost extra...).
The new code is here. I plan on adding color coding for muted/unmuted callers and to experiment with much more of the AMI features.
For giggles, here's a screenshot. That's my son dialed in via a SIP hardware phone, me dialed in via SkypeOut (via IPKall and FWD), while .call scripts pull in a Liquidsoap-generated stream from Icecast and push the resulting conference stream back to the same Icecast server.
Monday, November 19, 2007
Coming up for air
Hopefully, I should have everything done this coming weekend.
Sunday, November 18, 2007
chk_vm_pwd.agi
exten => *122,7,GotoIf($["${result}" = "0"]?20:30)Note the one less left-bracket ("[") before ${result}.
Saturday, November 17, 2007
pyTivo
Monday, November 12, 2007
Not a small problem.
While this sort of paper doesn't cause problems directly, it is the sort of thing that others build upon, often ending with "nice" additions to security toolkits. I wonder how long it'll be before NIST responds....
Update: the paper is here if you don't want to wade through Slashdot.
Saturday, November 10, 2007
Shmoocon attendance
Telmnstr is campaigning for a Hack or Halo project. Any thoughts? I've got a collection of junk box kruft that I'm willing to donate as parts or prizes.
Tuesday, November 6, 2007
Cell phone jamming
- What's your justification?
- Are you jealous that you're not part of the conversation?
- Don't like that the girl likes to say "like", like way too much?
- Before you get into the "invasion of your space" argument, answer the question: "Where am I?" I'm willing to bet that you're in a public place and your personal space doesn't involve a cone of silence.
- Do you come from one of those broken homes where "silence at the dinner table" was a rule? If so, then I'm sad for you. I come from an active family that the earliest we'd see each other as a group was dinner time. Aside from a few spats when we were younger, it was a time for communication.
- Are you that much of a control freak?
When you press that button realize:
- You're breaking a Federal law each time you push that button, risking fines up to $11,000 ($10,000 for jamming, the rest for possession and use of contraband)
- You're also risking a civil suit from anyone who's conversation you interrupted (think doctor's talking to emergency room). Jammers are rarely directional, especially the cheap ones. A thirty foot range means sixty feet by sixty feet (i.e., everyone in the restaurant, and then some).
Yeah, there are a few places where cell phone use can be seen as inappropriate, such as church, a movie theater, or class. However, let me point out that it is not you, with your butt in the chair, that has the right to enforce any such rule. It is the responsibility of the paster/priest, theater owner, or instructor to make and enforce the rule. Anything that you do, including saying "Hang up that phone!" is beyond your jurisdication and may be construed as a form of assault (look that one up). It falls under "The management reserves the right to refuse service..."
You want silence, go sit somewhere where the business owner prohibits the use of cell phones (it's his jurisdiction, not yours). If it's a public place, you're S.O.L.
You cell phone users. If it's a place where quiet is the norm, it's okay to answer your phone, just take the conversation outside as soon as possible. It's the polite thing to do and it'll help keep the etiquette nazis off of the rest of our backs.
Me? I'm using another entirely legal device. If you use a jammer in plain view, I'm taking a picture and hoping it's good enough to convict you. If you're yelling into the phone in a place where quiet is the rule, I'll take a series of pictures (hey, you're acting strange in public), choose the best one, and submit it to the Craption Contest.
Monday, November 5, 2007
pyTivo
In any case, pyTivo allows me to push media from my computer (vidcasts, podcasts, SageTV recordings, etc.) back through the TiVo.
The bad news is that the program actually has to load the media onto the TiVo. The good news is that you can start playing it a few seconds after the transfer starts (good for large vids!).
I did have to monkey with the config file just a bit. I had to enable the beacon and change it to the broadcast address for my network (vice 255.255.255.255). Note: the Cheetah Namemapper warning supposedly can be safely ignored.
In any case, I can now watch vidcasts on my TV without having to use the funky podcast client built into the TiVo interface. Even though I can play music through there, I don't have a decent sound system connected to that TV so I probably won't use that one much. Also, lets not forget the ability to pull files off of the TiVo with the web interface (backups!).
Got mine
Saturday, November 3, 2007
A web interface for LiquidSoap
Wednesday, October 31, 2007
Shmoo Tickets
Sunday, October 28, 2007
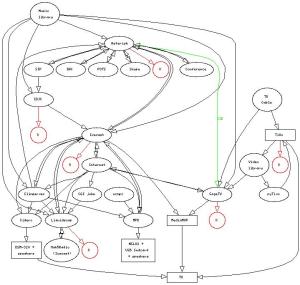
Geekin' Hard!
At some point, I've tested each part. Most of it is still connected and available on demand (from inside the network). About the only part that I've disabled is the IDJC piece (it generated too many audio "artifacts").
The parts in red are record functions. The piece in green is Asterisk passing CallerID info to SageTV. The rectangles are hardware. The circles are not.
Pieces that play MP3 files from the library:
- Asterisk
- Icecast
- IDJC
- Liquidsoap
- SageTV
- Slimserver
- Asterisk
- Cidero
- Icecast (via relay)
- Liquidsoap
- MediaMVP
- MPD
- Slimserver
- Asterisk
- Icecast
- IDJC
- Liquidsoap
- MPD
- Slimserver
- Asterisk
- Icecast
- Liquidsoap
- MPD
- SageTV
- Slimserver
- TiVO
For video, my favorite is SageTV. It records scheduled and timed video, has a "hackable" web interface, allows all sorts of plugins for additional features, and can stream to hardware and software clients in the local network. It generates RSS feeds for recent recordings and the upcoming recording schedule. For those that aren't familiar with SageTV, think MythTV with a lot more polish and a lot less set-up work.
Note: this is all Linux-based but there are Windows versions of just about all of the programs. The amazing part is that I rarely see my dual core system get below 95% idle.
Wishlist (things I want to experiment with in the next year): X-10 interface, home automation, some sort of podcatcher, IAX to a friend's Asterisk box, a hardware-based phone, motion detection with cameras, hosting and/or recording a live conference call, amateur radio.
Disclaimer: I do nothing illegal with this set up, though the capability is definitely there. Diagram courtesy of GraphViz's dot program.
Saturday, October 27, 2007
Wednesday, October 24, 2007
Asterisk to Icecast
Saturday, October 20, 2007
Adding Custom Searches to SageTV
Thursday, October 18, 2007
Missing the old days?
If you know of anyone pining for the old days, especially if they're obnoxiously spouting off how cool Fidonet was and such, you can point them (telnet) to bbs.hak5.org. There, the Hak5 bunch has set up a BBS so that people can be reminded just how spare the interface was.
A few things missing from the experience:
- the text should be printing at 300 baud (about the speed that the average fourth-grader can keep up with)
- the connection should drop out periodically (think of it as beind randomly logged off against your will)
- the text files need more Ctrl-G's
I do miss those Ctrl-G's.
The devil's in the details
- use gcc, not make or cc
- when you run the program what is displayed?
- can you do anything (hint: type ls or whoami)
- if you hit Ctrl-C and run "ls -l", what do you see?
- re-run the program and try to answer these questions again
Note: success may be specific to the version of the OS being run on the target machine. Your mileage will vary depending on a number of things (hint: the classroom lab is a controlled environment (i.e., each target is exactly the same)).
Enjoy! But you should probably get your homework done first. You may spend more time than you should getting the exploits to work in your home labs. If you're frustrated, please note that Rob usually isn't adverse to you coming in when there isn't a class in the lab. Just check in with one of the techs in the fishbowl.
Tuesday, October 16, 2007
Kernel upgrades and HTPCs
Hak5 bumpers
Friday, October 12, 2007
LiquidSoap web interface
Wednesday, October 10, 2007
What's next?
There's a case in the UK where a car repair business is being sued for copyright infringement because their mechanics are playing music loud enough that it can be overheard by others. Silly, no?
Even sillier, it's not the employees of the business that are being sued for the actual sharing of the music (by turning their radios on). Rather, it is the business being sued for facilitating that sharing. (Never mind that broadcast radio has already paid for the broadcasted content and that it is able to be heard by anyone with enough skill to operate a tuning dial or button.) Or will the employees be sued at a later date, once it can be determined whose radio played what song when?
What's next? Having to pay a service fee for riding the elevator because muzak was playing while you rode? Of course, the elevator company would have to record the number of riders and the distance (in floors) that each rider traveled.
NSLU2 Icecast Server
Monday, October 8, 2007
Configuration silliness
Sheesh!
Sunday, October 7, 2007
NSLU2 Audio Redo?
Problem is that I'll need to use the current NSLU2 (with the audio interface) and another with Icecast running on it. I running the risk of more people (at the meeting) being fascinated with the NSLU2's than the LS scripts I'm trying to show off. (Notes will be in the wiki shortly.)
Wednesday, October 3, 2007
Liquidsoap update
I can attest that chaining Sky.FM-->SlimServer-->LiquidSoap-as-a-player works very nicely. Even the metadata being passed across from Sky.FM is handled properly, and neither processor got below 95% idle on the dual core, even with all of the other crap I run on the box (SageTV, fetchmail, etc.). That's saying a lot as it appears that both Slimserver and (possibly) LiquidSoap are doing a bit of transcoding on the fly. The one drawback to this so far is SlimServer's built-in delay (5 or so seconds). I'll need to read up on that.
It's obvious that simulcasting (rebroadcasting/redirecting) a stream is going to be simple. I need to play with the mixing features now (think "periodic jingles" mixed into an open conference call). If I can come up with an interface to Asterisk, you can consider me as having thrown IDJC in the round file.
Oh! If anyone's interested (and for my own notes), the syntax is
liquidsoap 'out(input.http("http://192.168.1.175:9000/stream.mp3"))'
LiquidSoap
In attempting to troubleshoot IDJC, I discovered a new streaming tool called "LiquidSoap". To quote the website, it is basically a "general purpose audio streaming tool, designed as a script language, which allows you to build complex webradios".
While the toolset is still considered to be in development, I was able to get streams going via a local radio site (okay, hak5radio) in 30 minutes of installation/reading, vice the 2 months of on and off frustration with IDJC.
In reading some of the docs, there's quite a few interesting features: on-the-fly transcoding/normalization, misc. scheduling features, drop-on-live-input, an IRC bot interface (with input!), and even a (in-development) touchsreen interface. Definitely something for the home theater enthusiast that likes to tweak his/her own stuff!
Monday, October 1, 2007
Self-referentialism
(heh) Cutting edge does have its drawbacks...
Sunday, September 30, 2007
ZoneMinder update
Wednesday, September 26, 2007
BSQOTD
Uh, yeah... While I concur that wireless is being used inappropriately in some areas (see my comment on his page), that statement didn't help Dale's argument much. (heh)
Getting the customer to speak
I'm not saying that I don't believe that the condition exists. People (and therefore organizations) tend to take the path of least resistance, so if the penetration testers don't ask, the customer is not going to offer up the information.
My surprise is that the question just doesn't come up. It may be because I'm the type to take a packet sniffer to a CTF contest. (Yeah, one of those that thinks that CTF is a spectator sport.)(I have Don M. at ODU and S-14 (hiya Pete!) to thank for that "bad habit".) To me, the "What did you see?" question is just so obvious that it's a "must ask".
I can also see how organizations fall into the practice of not participating in their own penetration testing. It may have something to do with that other form of security testing called the vulnerability scan. It's usually performed more often and requires no input from the customer, except during the remediation phase, and that is usually an internal process (e.g., the CIO may have some "'splaining to do" to the CIO).
The Hansen/Ranum/McGraw reference to the "badness-o-meter" is a good one. If your pen-testers have anything other than "we don't know" at the top end of the scale, the data they're providing about your level of security may be suspect. Pen-testing is an inverted business-model. The best you can hope for is: "We don't know. We failed." A few things to keep in mind:
- This doesn't mean that someone else doesn't already know
- It also doesn't mean that they won't know tomorrow or the day after
- To quote a semi-cliche: "Security is a process, not an end state." (Dr. M. E. Kabay, 1998)
- By extension, a pen-test is a snapshot of that process, not of an end state
Sunday, September 23, 2007
Security by fashion statement
My initial thought was "somebody is selling something". Upon reading the article (follow it to the daily blog to see the link), I discovered that I wasn't wrong. The reason for the articles existence was to make you overly paranoid about your users and get you to buy something to counteract the threat. If that purchase just happened to be the product mentioned in the article, so much the better!
My second thought was that this was another in a long line of "security by fashion statement" (bowel) movements. Think about it. We have a number of firms where "analysts" (those that aren't practitioners but are somehow (mysteriously) more knowledgeable) declare that one security method is "auld schoole" and there are much better, more modern, methods of performing such and such a function.
It's quite annoying. In the past five years, we've been told:
- IDS's are dead, IPSs are better (thank you Gartner)
- Anomaly detection is better than IDS/IPS
- the firewall is dead
- the perimeter is dead
- SSL are the best VPN's
- stateful inspection is better than application proxies
- deep packet inspection is better than application proxies
- application proxies are better than stateful inspection, packet filters, and deep packet inspection (What? You missed the resurrection of proxies by Gartner?)
And now you need to be so paranoid that your users' every key stroke needs to be monitored and analyzed for intent (yeah, that works well), to the degree that you must come up with "termination plans"? Oh and, by the way, we just happen to have this nice product that'll automate this process and make your life much easier.
A much better approach would be to have a realistic security policy and to use the tools you already have, especially the one behind your eyeballs. Most "insider threat" incidents are considered corporate embarrassments not because the incident occurred but rather because they weren't detected until after the fact. The majority of insider abuse is readily apparent, either in the virtual world (in log files) or out in the real world (people tend to talk about what so-and-so is getting away with).
Attempting to totally automate the process, in either the virtual or real worlds, is just a way of abstracting yourself further away from the problem. Network monitoring and management of people have at least one thing in common, they "automate" poorly in that an automated process can only handle "known" issues. Unique issues can always crash automated processes. (It's why we have web-based time sheets but still have entire HR departments.)
You want to properly deal with the "insider threat"? It's easy. Show "trust" in your users. It's okay to "verify" but a certain degree of monitoring but it has to be at a level that your users are comfortable with.
Also, use the tools that you already have. Automated log file reduction is fine, but you still need human review of the remaining entries.
The firewall, the IDS, and security boundaries are still valuable. So's enforceable policies, deep packet inspection, stateful firewalls, and anomaly analysis. They each have their place in your toolset.
Companies such as Gartner like to bank on the fact that you've forgotten that none of these technologies are mutually exclusive. While "layered defenses" may be an offensive term to some, the existence of multiple protections which co-support an overall security policy is still a good idea. Just don't take the human factor out of it.
I've got news for you: If you run a totalitarian environment (AKA micro-manged, micro-monitored), every single one of your users will be evil and you'll end up wondering why your organization has such a high turn-over rate.
Save your cash. Also, keep in mind that the less flexible a system is (the degree of tolerance it has), the more brittle it is and the more spectacular the failure will be when it does go. This goes for machine systems as well as for people.
Thursday, September 20, 2007
FC7, an NVidia 6340 LE, and a SyncMaster 940BW
Not any more. I've needed to install Fedora for a few toolsets that I've wanted to play with and finally had the time (I took a day off) to install Fedora and figure out how to get the video configured properly (usually it'd come up with bars on the side and no mouse cursor).
Fixing both of those problems was pretty straight forward. The mouse involved turning off the hardware driven cursor. The video involved trashing the Fedora drivers and grabbing the binary off of NVidia's site and letting it compile new modules.
I've stuck my notes in the wiki.
Sunday, September 16, 2007
Tools
Saturday, September 15, 2007
Shmoocon CFP is open
Step 2: Annouce CFP (in progress)
Step 3: Devise ticket sales scheme that (hopefully) won't anger the natives (TBD)
Wednesday, September 12, 2007
Memory limitations
Monday, September 10, 2007
Need to choose
The IPv6 work would be more directely related to the "Attacks" class. Rob suggested it knowing that I'm one of the few students with IPv6 at home.
I'm interested in the FastFlux problem but I'm wary of where it might lead (remember, the problem is based on problems within the domain registration infrastructure). Then, too, it may also run into one of any number of dead ends as there is a massive bureaucracy between ICANN and the hosting providers, with the registrars in the middle). Without the ability to subpoena a number of people, investigation is limited to what you can extract via the local terminal window. Corruption at the hosting provider or registrar makes it that much more difficult.
I'm a bit discouraged but not yet put off by that. Initial investigation of two FastFlux domains shows a massive number of systems attached to the Storm Worm (amazing since, for most of those boxes, someone had to click on "Click here" to get infected).
In any case, I've got to choose soon. Rob's deadline is coming up fast.
Zoneminder
So far the install has included:
All this before even compiling pvrusb2, MythTV and Zoneminder. Luckily, most of the above could be done by sitting down at the console every 20 minutes or so. It is a bit tedious though. Makes me think that I should have tried one of the Zoneminder LiveCD's first. (I didn't because there's a number of things I want to do that probably aren't in the LiveCD.)
Thursday, September 6, 2007
Where's stupid?
How about a thousand?
Ten thousand?
Seven hundred fifty thousand?
It's actually very easy to do. Remember Gnutella? Google does. Sheesh! And you thought the RIAA had to do something sneaky to get it's target IP addresses.
Hint: If you must view those links, I recommend clicking on the "Cached" link as most of those entries are offline at the moment.
Wednesday, September 5, 2007
Request for help
Any help (or pointers to documents other than the ALSA wiki) would be greatly appreciated.
Sunday, September 2, 2007
New(er) Asterisk Book
Shmoocon '08
Saturday, September 1, 2007
Porn Glossary?
I learned about all this via the installation of Google analytics. It adds a number of behind-the-scenes accounting features that have confirmed a number of suspicions about visitors to the site and has pointed out a few other new data bits (such as SpraakService).
Looks like the wiki may have picked something up in the translation... (heh)
The end of a long week
In any case, the CTF was today. I captured two of the team flags. We didn't take first (or even second) but we had a very good time as we were doing it (translation: the rules didn't prohibit adding content to the web pages). To whomever it was that left the ptrace-kmod exploit laying around in one of the user accounts, thank you. I was able to repair the bug in the source code and use it.
In any case, my son is fine (if you don't count him being a 200 pound assinine eating machine when he's on steroids) and I have roughly three months to recert GSEC and six months to do my GCIH.
I also picked up quite a few topics for research during the SANS class (tracking FastFlux, tracking browser header alteration by spamware, etc.). I'll need them as I decided to crash Rob's Attacks class since we couldn't get enough participants for the Continuing Case Studies in Forensics. Maybe next year?
Thanks to the others in the fourth row/left side of Ed Skoudis's class this year. I enjoyed the class/exercise.
Tuesday, August 28, 2007
When USB ain't
One student had a high-end laptop with a number of USB ports on the side and back surfaces. Upon plugging the USB GPS into the side port, he noticed that the LED was quite dim (where other students' LEDs were bright). Thinking that he might have a bad GPS (they're available online for about $35.00), he borrowed the next student's GPS. Upon plugging it in, it too showed a dim LED.
End result: two fried GPS's. Cause: Turns out the manufacturer modified the power spec for the side port, to allow for USB DVD drives.
I won't say who the MFR (feel free to use both definitions of that acronym) is, but you can bet that their entire line of products won't be on my list of prospective buys when it comes time to buy a new laptop. I shouldn't need to worry about my laser mouse burning a hole through the desk (and my leg). MFR's: stick to the dang specs! If you're going to modify a connector's spec, modify the connector too!
Sunday, August 26, 2007
SANS Va. Bch.
How high?
The trick is determining exactly where your two end points are. For most U.S. cities, this is easy:
- Go to Maporama.com and enter your address in the "MAPS" box in the upper left, then click on the little orange arrow on the bottom right of the box
- Maporama may present a list of possible sites. If so, find yours and click on it.
- The lat/long for your site will be in the "INFORMATIONS" box under the map. Write that down.
- Repeat the above step for your other end point. Put your lats and longs into a lat/long distance calculator to get the distance
- Divide your distance in half and use a Fresnel zone calculator like the one at RadioLAN. (Hint: the Fresnel zone is largest at the mid-point.)(Don't forget to use 2400 MHz!)
- Divide the results by 2 to get the minimum height of your antennas.
Keep in mind that this assumes no obstructions between the two antennas and that both antennas are the same height. If the obstruction is nearer one of the antennas and/or the antennas are different height, the math is a bit more complicated.
The above does make for a good off-the-cuff W.A.G. though.
Saturday, August 25, 2007
You can't do that!
Amazing. If Novell were a police officer and SCO a suspicious looking character whom Novell stopped near an alley, I think that SCO would be subject to a sobriety test after stating something like that.
You can't make this stuff up.
Thursday, August 23, 2007
Unintended consequences?
- it is vaguely worded. "Inaccurate" and "misleading" are undefined, meaning they are left up to interpretation, both by law enforcement and the legal system (meaning that it will be up to case law to determine the definition).
- the wording of the law allows for a non-judicial entity to interpret the law
- the law does not define who is allowed (or how) to monitor the Caller ID "system" (Remember, it is a loosely worded protocol agreed upon by a collection of "peered" communications companies)(Does the fact that I own/manage/use a number of Asterisk boxes make me a communications entity? An infrastructure owner? Am I POTS (see below)?)
- it strikes me as being worded like a statute (no need to prove intent) (but hey, I am not a lawyer so...)
- it is intended to protect an insecure protocol (with poor implementations) that was never intended to be employed as a legal form of identity
- Caller ID is not a universal service
- There's no definition of "POTS". POTS stopped being 100% analog lines and hardware switches decades ago.
- the wording of the law protects only a specific industry (POTS)
It is this last issue that caused the title of this post. Given the move away from POTS to IP-based services (POTS has been losing ground to special purpose (usually smaller) carriers for years. Vaguely worded laws get enforced in all manner of ways unintended by their authors. I think that this law may just push various user communities (industries in particular) away from POTS. (i.e., Caller ID will be whatever the company wants internally.
Organizations like autonomy in controlling what they have, especially internal infrastructures. I don't see this as improving organizations' relationships with "the phone company". Think about it. Anyone receiving a phone call from any one of 400,000+ phones internal to Microsoft (as an example) will probably only see "Microsoft" in the Caller ID, even though the capability is there to show "S. Jobs" (or whomever).
[Yeah, I know he doesn't work there.]
Hmmm... This may create a niche industry for Caller ID interfaces (internal call recipients see one thing, external another).
Monday, August 20, 2007
Congratulations Matt and Michelle!
Matt/Michelle: I wish you many happy years to come!
Wednesday, August 15, 2007
Spook Country
I've been attempting to read it only in dribs and drabs, putting off any heavy reading until I'm on a 12-hour trip coming up in the near future.
Sunday, August 12, 2007
Vista's Firewall
Oh come on! It's just a packet filter, and a poor one at that! They've tied Layer 4 to Layer 7 (specific applications have specific ports) but somehow skipped everything in between (protocol matching, state tracking, etc.). Where's the ability to add functionality (modules) as needed? How about some decent logging facilities?
While I do see the need to keep it simple (the majority of users can't configure a firewall, much less a WWVB-controlled clock), I disagree with the authors in that this is an absolutely royal piece of dung. This has less functionality than one of the pre-1.0 versions of ipchains (hint: a decade ago).
The majority of third party firewalls have much more capabilities. Unfortunately, only those companies who pay tribute to the OS maker are allowed to run their firewalls on Vista. "Advanced" is a relative term in this case because MS gets to filter its competitors.
And before I get accused of MS bashing again, the technology is not what is at issue here. This is "innovation" (i.e., salesmanship) from the marketing department (i.e., putting lipstick on the domestic Sus and expecting someone to kiss it). Anyone want to call "shennanigans"?
Saturday, August 11, 2007
WRT54GL and Kamikazi
In any case, after a number of failed attempts to reflash the APs, we gave up and went home. This morning, reading deep within the docs, I discovered the following method for pushing WhiteRussian RC6 on top of Kamikazi:
- Grab openwrt-brcm-2.4-squashfs.trx from the OpenWRT site. It is a generic firmware for just about any Broadcom chip set-based AP.
- Assuming that you have a Linux box, put that file in the root directory of your web server. I also changed the name of the file to openwrt.trx (for simplicity.
- Boot the AP into failsafe mode (Press either the front or back reset buttons after the DMZ LED lights up. Hold it in until the DMZ light starts flashing.)
- Telnet to 192.168.1.1 (your box has to be within the 192.168.1.x IP range). Note: it may do nothing for a moment. This is because the AP is attempting to perform a DNS lookup, for which there is none. Just let it be. The DNS query will time out and the command prompt will show up.
- Run the following command: "wget http://192.168.1.175/openwrt.trx -O - | mtd -e linux -r write - linux" (without the quotes and use the IP for your box). Again, it will stall while the AP attempts to do a DNS lookup. Let it be, it will start moving again. Once the file is fully downloaded, DON'T DO ANYTHING!!. The AP will write the firmware to memory and then reboot itself. It'll be safe to use once the power light stops flashing and the DMZ light goes out.
- Point a browser at 192.168.1.1 to be sure it's working. Click on Status (or one of the other options). It should prompt you to enter a new password for root.
- Click on the "System" link at the top to take you to the System Settings page. Change boot_wait to "Enabled". Click "Save Changes". Click "Apply Changes". (You may want to SSH or Telnet into the box to verify that the boot_wait is enabled (Use "nvram show|grep boot").
- Not to jinx things, but it may be a good idea to re-reflash the firmware with a dedicated version of OpenWRT, using the TFTP method.
After that, it's up to you. Visit the OpenWRT Wiki for ideas.
Thanks to whoever it was that added the trick to the OpenWRT's Installing - OpenWrt page. Jon Dowland, maybe?
Put on your hard hats!
I wonder if any criminal cases will arise from this. Civil cases most definitely.
Update: the first link above (to Groklaw) is offline at the moment, probably due to a massive number of people trying to read about the decision.
Thursday, August 9, 2007
Wednesday, August 8, 2007
Asterisk Users Conference Call
Monday, August 6, 2007
Prime Time Tonight
Sunday, August 5, 2007
OSWA Assistant
Adding default content to new wiki pages
Saturday, August 4, 2007
Startup script for SageTV
Friday, August 3, 2007
San Diego
Saturday, July 28, 2007
Slimserver/MPD boot sequence
Wednesday, July 25, 2007
IDJC
I've got a couple ways of experimenting with it. One with an internal Shoutcast server, streaming to the nodes in the house. The second one involves taking advantage of an open spot on the Hak5Radio server (if those guys will tolerate it). I've been told to try a mixture of Southern Baptist Gospel and Leonard Cohen. (JK! Just checking if you guys are awake.)
Monday, July 23, 2007
Spook Country
Sunday, July 22, 2007
Magic quotes and MediaWiki
However, thanks to this page (sorry, I don't read Russian), I have the new work-around.For those interested, add the following as the second line in index.php: "ini_set('magic_quotes_runtime',0);". You may need to add it to the index.php in the config directory too.
If this helps, please pass it on.
Saturday, July 14, 2007
Captive portal notes
Wednesday, July 11, 2007
Telent and SMTP
One thing not mentioned is that this technique can be employed to create a whole lot of evil. While outward facing SMTP servers are normally protected against this kind of abuse, internal Exchange servers usually aren't. More than one security manager that I've worked for has received periodic beat-your-admins messages from the Easter Bunny and Santa Claus. (Disclaimer: I rec'd permission to do this beforehand!)
Tangents
Sunday, July 8, 2007
Linksys WRT54G Ultimate Hacking
WiFiDog and Squid
iptables -t nat -I WiFiDog_WIFI2Internet -i eth0 -m mark --mark 0x2 -p tcp --dport 80 -j REDIRECT --to-port 3128
I got quite frustrated in trying to script the table entry, post startup. So much so, that I attacked the source code and figured out the following, slightly buggy, patch:
iptables_do_command("-t nat -I WiFiDog_WIFI2Internet -i eth0 -m mark --mark 0x2 -p tcp --dport 80 -j REDIRECT --to-port 3128");
When you're building WiFiDog, after you've run the autogen script and before you run make, add the above to wifidog/src/fw_iptables.c, after the last line containing "TABLE_WIFIDOG_WIFI_TO_INTERNET". After running "make" and "make install", all you have to do is turn on transparency in your Squid box.
I said "slightly buggy" because, by itself, it prevents admin logins. I managed a work-around by adding a high-port listener to Apache (I was pressed for time). When I'm able to access the system again, I think that the fix would be to add another line, just before the one just added, that prevents redirection of traffic to the auth server.
I'll keep you posted. I'm annoyed enough that I'm looking at tweaking the source code.
Friday, July 6, 2007
Hey brother! Got some spouse points you can spare?
I arrived home from work yesterday, to a house that had been without power for a little over an hour, to a wife with blood in her eye. Seems that when the power went out, a number of devices started complaining about lack of power: the burglar alarm, the smoke alarm, and a small unobstrusive UPS that I had snuck in during a long-running moratorium on hardware purchases.
"Make it stop." was all she said.
After the power came back, I quickly configured Nut (Mandriva had detected it during the install and had loaded it) and installed KNutClient. The bad news is that the beeper is hardwired (it won't turn off). The good news is that I now have another set of metrics to play with.
Now I just need to figure out how to explain that there's no feature to silence the beeper without losing the UPS entirely.
Hmmm... Maybe an upgrade to a better UPS might be possible?
Wednesday, July 4, 2007
WiFi Portal
Monday, July 2, 2007
Injured list
It makes for slow going, enough so that I'm relying on spell checkers to catch my mistakes. If you've ever tried to do this, it can create some very silly sentences.
Please, if you see any weird spelling/grammar, point it out.
Saturday, June 30, 2007
SlimServer, Cidero, and DMS-320 Notes
Monday, June 25, 2007
Cidero XP
- Downloaded CideroApps_windows_1_5_3.exe (the first one on the list)
- Tried to run it. Got prompted to install a suitable JRE.
- Went to Sun and downloaded the "Java Runtime Environment (JRE) 6u1" (online install version)
- Installed the JRE ("Typical Setup")
- Ran the install tool for Cidero (used default settings)
- cd'd into C:\Program Files\Cidero\db\radiodb\AllStations\
- Copied AmpedOut to SlimServer
- Right-clicked on SlimServer and chose "Open with" and Notepad
- In the dc:creator and dc:title lines, changed "Amped Out" to "Slimserver"
- Changed the dc:description content to "Joat's Slimserver"
- Changed the URL in the dc:relation line to http://192.168.1.175:9000
- Changed "x-scpls" to "mpeg" in the first res line
- Changed the bitrate from 16384 to 8192. 16384 is for playing 128kb streams, 8192 is for 64kb streams. Most of the podcasts I listen to are 64kb. You can add additional res lines for different bit rates but it might be a good idea to identify them with different names (you'll probably need separate playlists on the Slimserver also)
- Changed "http://www.ampedout.net/ampedout-128k.pls" to "http://192.168.1.175:9000/stream.mp3" in the first res line
- Delete the second res line
- Saved the file and exited Notepad
- Started RadioServerProxy from the Start menu
- Started MediaController from the Start menu
- Under Media Servers in the "Cider UPnP A/V Controller" Window, click on CiderRadio
- Under CiderRadio, click on the little toggle next to AllStations
- Under AllStations, click on the toggle next to SlimServer
- Click on "Slimserver - MPEG/64k" (this will add it to the right-hand window)
- Assuming that your DSM-320 is turned on, it should show up in the "Media Renderers" window as "My Media Player" (if you didn't change the default setting on the DSM-320). Single click on that to bring up the player window.
- Back in the "Cidero UPnP A/V Controller" Window, under the Music Tab (right hand side), single click on the Slimserver entry to highlight it
- Click on the "Add Tracks to Play Queue" button. This should add Slimserver to the playlist in the "My Media Player" window
- Click on the Play button in the "My Media Player" window. You should see the timer start counting.
- Make sure your Slimserver is running. Point a browser at http://192.168.1.175:9000 (or whatever the IP address is where you installed the Slimserver software.
- There should be an IP address in the upper right-hand corner of the browser. Make sure that it's the IP for the system where you installed Cidero.
- Choose a music source in Slimserver and add it to the MusicPlayer playlist by clicking on the little play button next to your selection.
- Click on "Play" under "Music Player".
- If the counter in the Cidero "My Music Player" window is incrementing and you don't hear any sound, wait a minute or so. There will be a 5-10 second delay between hitting play and hearing sound. If the no-sound situation persists, make sure that something is in the Slimserver playlist and that the IP address for the computer where you installed Cidero is installed.
- Don't forget to bring up the Slimserver web interface, select your computer's IP in the upper right window, add music/podcasts to the playlist (bottom right) and click "Play" under "Music Player"
- Go see if you hear any music coming out of whatever the DSM-320 is hooked to.
I'll do a short video on this (like IronGeek) if anyone's interested.
Sunday, June 24, 2007
MS Surface spoof
Another thought: this is an interface for non-geeks. I mean, how many times can you reach for objects, in a manner such as those in the video, before your shoulder gives out?
Face it. Power geeks work/play by moving as little as possible. Sometimes by twitching.
Logitech USB Headset
Thursday, June 21, 2007
New Wireless Distance Record
Saturday, June 16, 2007
SlimServer + Cidero == DSM-320 Streaming
- Install the Java Runtime Environment.
- Download Cidero and install it as per site directions.
- cd into the db/radiodb/AllStations/ folder.
- Choose one of the files and copy it to SlimServer.xml. Edit SlimServer.xml. The "res" line is the only important one. It should read something along the lines of http://192.168.1.175:9000/stream.mp3
- Delete any other "res" lines.
- Check the file permissions. Make sure that SlimServer has the same owner and permissions as the other xml files in the same directory.
- If Cidero is already running, kill it. (Stopping and starting from the main menu does not work. Kill the binary.)
- Fire up SlimServer.
- Start Cidero and find the SlimServer entry (you probably should customize the other data in SlimServer.xml to make it easier to find)(or delete some/most of those other radio stations).
- Use Cidero to tell the DSM-320 to start playing the stream (you have to choose the feed, select the renderer, add the feed to the renderer's play queue, highlight the line in the renderer's playlist, and hit the renderer's play button).
- Go check your DSM-320. It should be playing whatever's being passed through the SlimServer.
Notes in the wiki shortly.
Wednesday, June 13, 2007
Where's are the bugs?
Are we sure who's at fault here? I'm not.
Tuesday, June 12, 2007
Slimserver + MuSE + Shoutcast
In thinking about running a client for either end of the house (small sound system in the bedroom, bigger sound system in the den), I needed to test if two could be easily slaved to the Slimserver.
Following the Streaming from Slimserver to Icecast howto from the Slim Devices web site, I was able to stream from LastFM to the Slimserver to MuSE to Shoutcast to the two clients, one running mpd, the other running vlc. (Read the howto for the description of why MuSE is needed.)
Keeping in mind that all of this software was running on a moderately powerful dual core system, I have the following statement (recommendation?): the configuration is "doable". However, I don't recommend it for the less-than-heavy geeks as it's definitely a finicky setup (it's not low maintenance).
Most of the issues I experienced (segfaults and just-not-working situations) centered on MuSE. Does anyone know of a workable substitute for MuSE (the Multiple Streaming Engine, not the publishing environment or the midi sequencer)?
Sunday, June 10, 2007
NSLU2, MPD, SlimServer
Thursday, June 7, 2007
Jaiku
Next step: figure out how to export SageTV feeds into Jaiku.
Tuesday, June 5, 2007
Skype Asterisk Update IV
If anyone can recommend a better Skype-to-Asterisk bridge method, please let me know. In the mean time, I will experiment with whatever I can find and will post my notes here.
Saturday, June 2, 2007
Wednesday, May 30, 2007
SageTV Favorites
Tuesday, May 29, 2007
Skype Asterisk Update III
The short version: tenative (I haven't proven it yet) kudos to Bruce Nepple for this post which discusses setting VNC's timeout option. Hopefully this will fix it.
Saturday, May 26, 2007
Editing the Sage menu
Hopefully this will head off any further questions...
Friday, May 25, 2007
MPD interface
It works okay without modification (be sure to edit the "host" entry in both index.php and playlist.php) but I found the text-only interface to be a bit too spread out. So, I replaced the text in his links with graphics, reordered them, changed the link colors, and added a meta refresh to index.php.
The end result is a bit cheesy (I need to find a decent set of graphics to "skin" this with) but it's functional:
Skype and Asterisk Update II
Tuesday, May 22, 2007
Skype and Asterisk Update I
- the keypad within the Skype client produces DMTF which can control/respond to Asterisk
- calls via SkypeIn do not
- voice applications running on Unbuntu-based VMs tend to steadily degrade over time (but probably can be fixed)
- the personal version of Chan_Skype is designed so that it only works with one license per machine (i.e., if you want multiple channels, you have to buy the business license which costs 5x more per channel)
- the Chan_Skype people need to work on their versions (currently limited to outdated versions of Ubuntu and Fedora)
In short, I like the product but really hate its shortcomings.
Monday, May 14, 2007
Skype and Asterisk
For now, let me say that there are a number of drawbacks which some may be able to live with, some not. For a $20 license, I don't consider it to be too bad of a product.
Sunday, May 13, 2007
Busy week
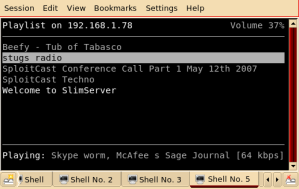
Shouts to the Sploitcast crew who let me sit in on a conference call. The call actually went for 4+ hours today and I think that wlc already has it edited back to about an hour. Whether my comments survived or not remains to be seen. It was fun experimenting with TalkShoe and Skype though.
To tell the truth, I mostly lurked in the call. I was actually working on getting a NSLU2 reflashed. Below is a screenshot of the final product (NSLU2 runing MPD which is listening to various streams, including the SlimServer on my desktop).
Monday, May 7, 2007
Life's little lessons
I then attempted to use the card online, at a site that uses PayPal to process customer purchases. My card was denied. In calling AmEx to find out why, I learned the following: the card is only good at sales entities which are direct customers of AmEx. They won't process "third party transactions" such as PayPal. When I asked for my money back, they offered me $15. ($28.95 minus the $3.95 processing fee, minus the $10 refund fee.)
I've decided to keep the card. I'll find somewhere that accepts it (mebbe Starbucks?). However, I'm going to put about $3.95 worth of effort (this post should amount to that) into letting other people know about my experience with AmEx's Gift Card service. I should probably note here that neither their site nor the TOS document that came with the gift card talks about refusing to work with third party services (specifically PayPal). The closest the TOS comes to that is disavowing responsibility if the Merchant declines the card. (In this case, AmEx declined the transaction, not the merchant.)
Bite me, AmEx.
Saturday, May 5, 2007
Semester end
Monday, April 30, 2007
WTF
This may be one of those situations where a judge needs to get involved to correct the difference between the letter and the intent of the law. If the RIAA does go forward with this (and damages the podcasting community), I hope that the judge allows for damages and legal fees.
DVD Archiving
If so, expect this hole to be closed in the near future.
Saturday, April 28, 2007
Probes
Friday, April 27, 2007
Cooperation
Q: Who's Billy? A: You.
Having lived a number of years, the "if we all work together" is one of those phrases that sets alarms off in the back of my head. The hidden meanings usually include: you're expected follow the speaker's "vision", the willing are expected to force the unwilling, and you're also expected to sacrifice something yourself. Keep in mind that the sister phrase to "if we all work together" is "if you're not part of the solution, you're part of the problem".
The speaker's effort is one that goes counter to market forces. What he's asking is to force a single version of DRM upon a market that doesn't want it. Ignoring the fact that there is in-fighting over whose DRM should be used (driven by $$), this attempt is doomed to failure as you can only annoy your customers so much before they find new ways of entertaining themselves.
The entertainment industry is in a spot where they should be beating up pirates and "playing nice" with their legitimate customers, rather than beating up everyone. That spot? How about: that piece of entertainment in your hand is considered a license to view/listen an intellectual work (i.e., it's virtual) only until you attempt to view/listen to it via an "alternate" format (e.g., CD vs. MP3). Then, it's considered a physical product in that you have to buy the entertainment again if you expect to access it via that different format. It's becomes confusing in that, should the plastic become scratched, the industry won't replace it (i.e., the virtual license is subject to physical damage).
Is it any surprise that both sets of the music industry's customers (those that make the music and those that buy it) are experimenting with alternate methods to connect with each other. The incentive for doing so is that the music makers can get paid more for their work and the listeners get more work for what they pay?
Markets are slippery things. You can only squeeze one so hard before it squirts sideways and takes on a different form. Personally, the only commercial music I've heard in years (other than the occasional live BNL concert) was either part of a television commercial (I don't watch much) or came out of my car radio on the way to work (when there weren't enough podcasts to get through the week).
With apologies for the rambling...
Wednesday, April 25, 2007
Monday, April 23, 2007
Silverlight
I think that what we're seeing is yet another case of the media parroting without verifying.
Sunday, April 22, 2007
School Wiki going down
Thanks
Jon, good luck with the thesis!
Saturday, April 21, 2007
Asterisk AGI
SageTV Menus
Thursday, April 19, 2007
Cidero?
Anyone ever worked with it?
Saturday, April 14, 2007
AppleTV
- It's more or less locked to iTunes (bleh!)
- It runs hot, almost too hot to touch.
I'm not saying that I don't like it, just that it needs improvement (which some have already undertaken). While it is probably a good choice for first-time non-geeks, I'm going to stick with SageTV and my MediaMVP boxes.
Friday, April 13, 2007
HaloScan Weirdness
After troubleshooting for a couple nights, I gave up and set the target= tag back to what Haloscan suggests. Danged if that didn't fix it. It's going back to "annoying popup" status (it doesn't open a new pane in Firefox anymore, like I'd originally had it). Such is the risk when you rely on other people's code updates I guess...
Anyways, back to your irregularly scheduled blathering...
Class notes
Give me a few days.
Tuesday, April 10, 2007
Shooting of the messenger(s)?
In doing the tiny bit of research for this post, I noticed that there's another expansion module out for the card game. I loved playing the game on Saturday mornings (yeah, when I was single), though I never owned a copy. I think I may thank Steve by tracking down copies of the game+expansions and buying them.
Oh! Anyone want to start a pool on when SCO pulls the next weird thing? You don't have to name a specific event, the majority just has to agree that the event/incident is weird, strange, or amounts to conspiracy theory.
Wednesday, April 4, 2007
Bloglines subs
I'm now way over my self-imposed limit of 300 subscriptions. I'll be weeding out the list in the coming weeks. Enjoy!