Thursday, February 28, 2008
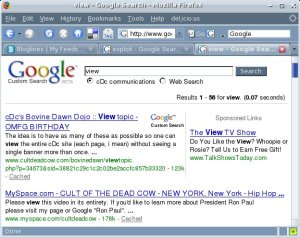
Goolag
Either one of those searches should have turned up hundreds, if not thousands of references to web cams. You can reproduce this "research" by going to Goolag and typing in "view" or "web cam" and then comparing it with a similar search via the normal Google interface (actually, Google will most likely block your search as an attempt at Google hacking, but it will report millions of hits).
Monday, February 25, 2008
VoIP Bandwidth Tester
Sunday, February 24, 2008
MPD on the NSLU2
Update: Running Icecast and MPD on the same NSLU2 may not be the best idea, at least if you're going to use the stock config files. I'm seeing almost 100% load on the box and the output to another system is quite bursty (about 3 seconds of silence for every 3 seconds of music). It's probably a good idea to put the utils on different systems (2 NSLU2s or a NSLU2 and a full-size computer?)(works nicely if I use my Asterisk service as a source). As I've built this for someone else, I don't have the resources (okay, or motivation) to tweak these.
For anyone that cares to, I will offer an account on the wiki if you'll post your tweaks.
Saturday, February 23, 2008
Icecast on the NSLU2
In short, I spent roughly four hours this morning installing various code on the NSLU2 and now have a working (I think) version of Icecast. Notes here.
If you're going to attempt the same build, it's probably a good idea to devote a Saturday to it cause it's not a simple process.
Now build MPD and write the start up scripts. I'll keep you posted.
Wednesday, February 20, 2008
Source Fource
- Can't we just buy a Happy Meal instead?
- Just how old are those guys in the marketing department anyways?
- How long before they receive an trademark infringement letter from Source Forge? (Do they think people have forgotten Mike Rowe Soft already?)
- Why is it that four of the figures on the web page appear to be actual pictures while the other three are cheesy hand drawings (including the ones for Vista and Office)? Were there delays in production?
Leverage
Tuesday, February 19, 2008
Zfone
Monday, February 18, 2008
Shmoocon 2008 - Day 3
- When Lawyers Attack! Dealing with the New Rules of Electronic Discovery (Benson)
- The Geek and the Gumshoe or Can Mathematics Solve Crimes? (Schearer, Thornton)
- PEAP: Pwned Extensible Authentication Protocol (Wright, Antoniewicz)
I left early 'cause I started feeling under the weather, nauseous on top of being tired, so I bought copies of various talks and got out of there. Good timing, too. By the time that I got back to Virginia Beach, I was down to nausea, shakes, and sweats. Haven't felt that bad since the last bout of food poisoning. Mebbe it's the flu? (No, I didn't do any of _that_ at Shmoocon. I was good.) I'm feeling somewhat better today but am definitely considering staying in bed.
Finally met CyberEagle at the SploitCast table. I'm bigger than he thought, he's younger than I thought. (Walc: I'll keep an eye out for more give-away stuff for next year.) Ran into Bob from work (shouts!). Talked with the Army cadet again.
No major surprises this year. Cisco took a beating though, with various people poking holes in VoIP implementations, network equipment, and various of their proprietary protocols.
All in all, another good conference from Shmoocon. Looking forward to seeing what 757 and the Sploitcast groups come up with for next year (this year was a bit weak in the Arcade).
Sunday, February 17, 2008
Shmoocon 2008 - Day 2
- Active 802.11 Fingerprinting: Gibberish and "Secret Handshakes" to Know Your AP (Sergey Bratus, Cory Cornelius, and Daniel Peebles)
- SIPing Your Network (Radu State, Humberto Abdelnur, and Oliver Festor)
- Passive Host Characterization (Matt Wollenweber)
- VoIP Penetration Testing: Lessons Learned (John Kindervag, John Ostrom)
- Advanced Protocol Fuzzing - What We Learned When Bringing Layer2 Logic to "SPIKE Land" (Enno Rey, Daniel Mende)
The SIP talk could have been better. They couldn't get the video for their demo to work so they had to talk about the tool they're working on, KiF (not sure what that stands for), a state fuzzer for VoIP. In some architectures, KiF can "borrow" authentication from other phones to be able to make calls.
The Passive Host Characterization was a bit dry (but still interesting). Matt is a former Trickler programmer for those that know what it is. He's posted a demo for his tool, PHC.
The VoIP Pentesting talk cetnered around some of the common configurations and shortcomings in VoIP architectures. They showed how VoIPHopper can impersonate a phone so that it can access an organization's internal network, often through the firewall (based on assumptions made during rollout of the infrastructure).
The Advanced Protocol Fuzzing talk wasn't what I thought it was going to be (Layer 2 discussions usually mean wireless) but it was interesting regardless. The group is basically working on reverse engineering and testing various Layer 2 management protocols, such as Cisco's WLCCP, using a tool called Sulley.
Here's a short view of the news/gossip from day 2:
- Ethan's walking without a cane! (For those that don't know him, he's taken a lot of ribbing for managing to generate a compound break in his leg via a Segway.)
- Rob and I got to talk with Dave Aitel and, later, with an Army Academy student (Dude, take one of our first three choices for intership! You'll get more out of it and you'll get to meet/know "interesting" people.)
- Southern Vriginia is well represented at the conference this year, having 757 (HRGeeks), Sploitcast, and Hak5 present. I managed to donate a couple items for one of Walcy's giveaways.
- Shouts to Squidly1! Who knew your offer would generate sales at the local Best Buy? (heh)
- I think hotel management finally found a couple groups that didn't "mix" badly with the Shmoocon attendees. There were actually two smaller conferences: one for "business resource managers" (salesmen) and one for Anime fans. No one really wanted to mess with the guys wearing tuxedos (they also kept to themselves) and the Anime fans were considered a bit weird by most of the geeks (though a 19-year old girl in a Sailor Moon outfit can be quite distracting). But seriously, they were wearing their costumes into the same restaurants that we were in and were making our freaks/rebels (you know, body piercings, tatoos, etc.) look normal. Most of the anime attendess just wore bunny or cat ears but some had full blown costumes which somehow were a mix of faux ancient Japanese, faux American Indian, and New York City hooker. (heh)
In any case, day 2 was fun. Got to catch up with a lot of friends that I hadn't seen since last year. I triend to hang around and particpate in the Sploitcast podcast recording but I was too tired and too hungry to stick around (my hotel is in Bethesda, MD).
Saturday, February 16, 2008
Shmoocon 2008 - Day 1
- Intercepting Mobile Phone/GSM Traffic (H1kari)
- Forensic Image Analysis for Password Recovery (David Smith)
- Baked not Fired: Performing an Unauthorized Phishing Awareness Exercise (Syn Phishus)
- Web Portals: Gateway to Information or a Hole in our Perimeter Defenses (Deral Heiland))
- Hacking the Samuri Spirit (Isaac Mathis)
"Intercepting Mobile Phone/GSM Traffic" was interesting though I got the impression that H1kari had dumbed it down to make it more interesting to a wider group. It was interesting in any case.
I felt the audience was a bit unfair at the end of David Smith's talk on password recovery. He had stated up front that it was a work-in-progress and that he was looking for other ideas. Basically his works comprises building attack dictionaries by extracting strings from memory space, passing them through qualifying filters (must be a certain length, must be from a certain (type-able) character set, etc.), and using the resulting dictionary in a much smaller brute force attack. (Rob! Something to include in the forensics class?)
Deral Heiland's talk on web portals had similar audience issues as it too was a work in progress. I guess we're an unforgiving bunch. It did remind us to pay attention to details when evaluating web services.
Isaac Mathis's talk well done (funny). It reminded me a bit of Johnny Long's talks on just about any subject. With a bit more practice, I think Isaac might just reach the same quality.
Overall, the conference is off to a good start (I wonder if there were any shenanigans last night). No suprises so far, security-wise. I ran into a few friends that I hadn't seen in awhile. Noticed that others were missing (maybe Saturday?).
Thursday, February 14, 2008
Shmoo!
Tuesday, February 12, 2008
Shrinkage
To paraphrase the television commercial: Sorry guys, I'm afraid I'm going to have to block you.
Note to self: start - 12 Feb - 392 subscriptions (now 383).
Monday, February 11, 2008
Shmoocon this week!
In any case, I'm looking forward to going. The 757 bunch will be there in force (someone said 30 of us!!?), counting those that have moved away but have remained in contact. Was there anyone that was forced to take the goon route this year?
Sunday, February 10, 2008
Xact and Yealink
Below is a capture from dmesg on the NSLU2.
input: Yealink usb-p1k as /class/input/input1
usbcore: registered new interface driver yealink
drivers/usb/input/yealink.c: Yealink phone driver:yld-20051230
usbcore: registered new interface driver snd-usb-audio
drivers/usb/input/yealink.c: urb_irq_callback - urb status -2
drivers/usb/input/yealink.c: urb_ctl_callback - usb_submit_urb failed -1
drivers/usb/input/yealink.c: urb_ctl_callback - urb status -2
drivers/usb/input/yealink.c: urb_irq_callback - urb status -2
drivers/usb/input/yealink.c: urb_ctl_callback - usb_submit_urb failed -1
drivers/usb/input/yealink.c: urb_irq_callback - urb status -2
drivers/usb/input/yealink.c: urb_ctl_callback - usb_submit_urb failed -1
drivers/usb/input/yealink.c: urb_ctl_callback - urb status -2
drivers/usb/input/yealink.c: urb_irq_callback - urb status -2
drivers/usb/input/yealink.c: unexpected response 11
drivers/usb/input/yealink.c: urb_irq_callback - urb status -2
drivers/usb/input/yealink.c: unexpected response 2
drivers/usb/input/yealink.c: unexpected response 4
drivers/usb/input/yealink.c: urb_irq_callback - usb_submit_urb failed -22
Port forwarding and SIP
Ignoring SIP proxies and external routing of calls, the immediate compromise is often forwarding a smaller number of ports and this can cause other issues if you're not careful about your server configuration.
Hint: if you only forward UDP ports 10000 through 10100, make sure to edit /etc/asterisk/rtp.conf so that "rtpstart" and "rtpend" have the same values. Otherwise, you'll often end up not being able to hear any incoming audio on SIP calls.
Friday, February 8, 2008
Firefly marathon
Monday, February 4, 2008
With apologies...
A much better approach would be to ask Rob to set up a demonstration network to show what can be done (e.g., mirroring a user's web surfing, intercepting a VoIP call, etc.). The main point is that all parties must agree to the monitoring/interception. Otherwise, it's very likely to be illegal.
Saturday, February 2, 2008
WTKR
Friday, February 1, 2008
11 Deceptive Truths We Think We Agree To
"1. Signature based desktop antivirus is an addiction, not effective security." This is one of the more offensive trolls. It's right up there with "the IDS is dead" and "the firewall is dead". Statements like this make sweeping assumptions about what you're trying to protect and what tools you're using to protect those assets. Sadly, signature-based anti-virus actually has the best ROI.
"2. The bad guys beat us because they're agnostic and we're religious. Complete and utter BS. The bad guys are in the lead because they're doing the majority of the research. It's a bad analogy to start because if the good guys were to ever "win", every bad guy would be either dead or in jail. Mebbe it's better to call it the "game of life"?
"3. Antitrust concerns force Microsoft to weaken security." Hahahahahahahahahahahahahahahahahahahahahahahahahaha...!!! Yeah, keep believing that Microsoft would give something away for free if they hadn't been sued in the past. Troll!!
"4. Vendors are like politicians - they lie to use because we ask them to." Wow. Uh, can I sell you something? Troll!
"5. We're terrible at talking to, or understanding, those that fund us." Uh, speak for yourself. Obviously, a good chunk of us understand "business-eese". Otherwise, the "industry" would have died of atrophy years ago.
"6. Security researchers need to grow up." Obviously Mr. Mogull has never seen someone else's name tacked onto his work, had his work denigrated in mainstream press, or was ever under attack from an organization that refused to believe that their product was ever anything other than perfectly secure. Troll!
"7. Security companies make more money when there are more incidents." True somewhat. However, Mr. Mogull seems to have missed the mark by claiming that the fastest way to grow a security market is to have a product ready when a massive exploit hits. It's a fallacy. The actual fastest way is to have a good marketing plan ready for when the next big exploit hits. You can go a lot further with a superb marketing plan and a crappy product than you can with a superb product and a crappy marketing plan. The day the day-stopping painful exploit occurs is when the lawyers make the most money. Followed by vendors as companies abandon certain products for others, followed by insurance companies as companies attempt to transfer the risk (look it up in your CISSP books) of future exploits. The security companies are somwhere after that.
"8. Network security is the result of a mistake, not an industry worth perpetuating." Either a troll or a cry for help. Network security is a need arising out of the fact that your company has a competitor. Ideally, life would be serene and no one would feel the need to steal your secrets. In the real world, someone sees some sort of profit (financial, emotional, relational) in breaking into your systems and changing something. Mr. Mogull's argument only holds water if you believe that somewhere out there, utopie exists.
"9. Disclosure is dead." WTF?!! Given their druthers, companies don't disclose sh#t. This is a massive troll that suffers from the wide-ranging, yet slowly moving pendulum of "accepted practice". Hint: a number of recent laws now require "disclosure" yet there's been a number of law suits which have forced limited disclosure of vulnerabilities and exploits.
"10. Momentum will destroy us, until it doesn't." Uh, huh? Innovation is a marketing practice. Operationalization is a marketing term (okay, vague rationalization for an irrational decision). The entire paragraph is basically a gripe that neither our employers nor the bad guys have remained static. Whiney troll!
"11. We can't fail." Mebbe as a whole. However, individual security companies fail often. They sometimes "take their customers with them". Just as the bad guys will never "win the war" (face it, it isn't a "war" where people die from every port scan), neither will the good guys. A much better analogy is to view it as a competion, where your goal is to "keep up".